Over 9,000 Wallets Hacked: A Review of the Solana Hack
Recently, Solana suffered from a huge hack event where the SOL and SPL holdings of many users were drained without them noticing. Following the Solana hack, crypto adopters have started to worry about the security of their assets stored in crypto wallets. Today, we will walk you through this incident and show you how we can guard against such security risks.
How the Solana hack happened
On August 3, Magic Eden, a Solana-powered NFT marketplace, posted a warning on social media that “there seems to be a widespread SOL exploit at play that’s draining wallets throughout the ecosystem.”
Soon afterward, OtterSec, a blockchain audit & security team, tweeted that “over 5000 Solana wallets have been drained in the past few hours.”
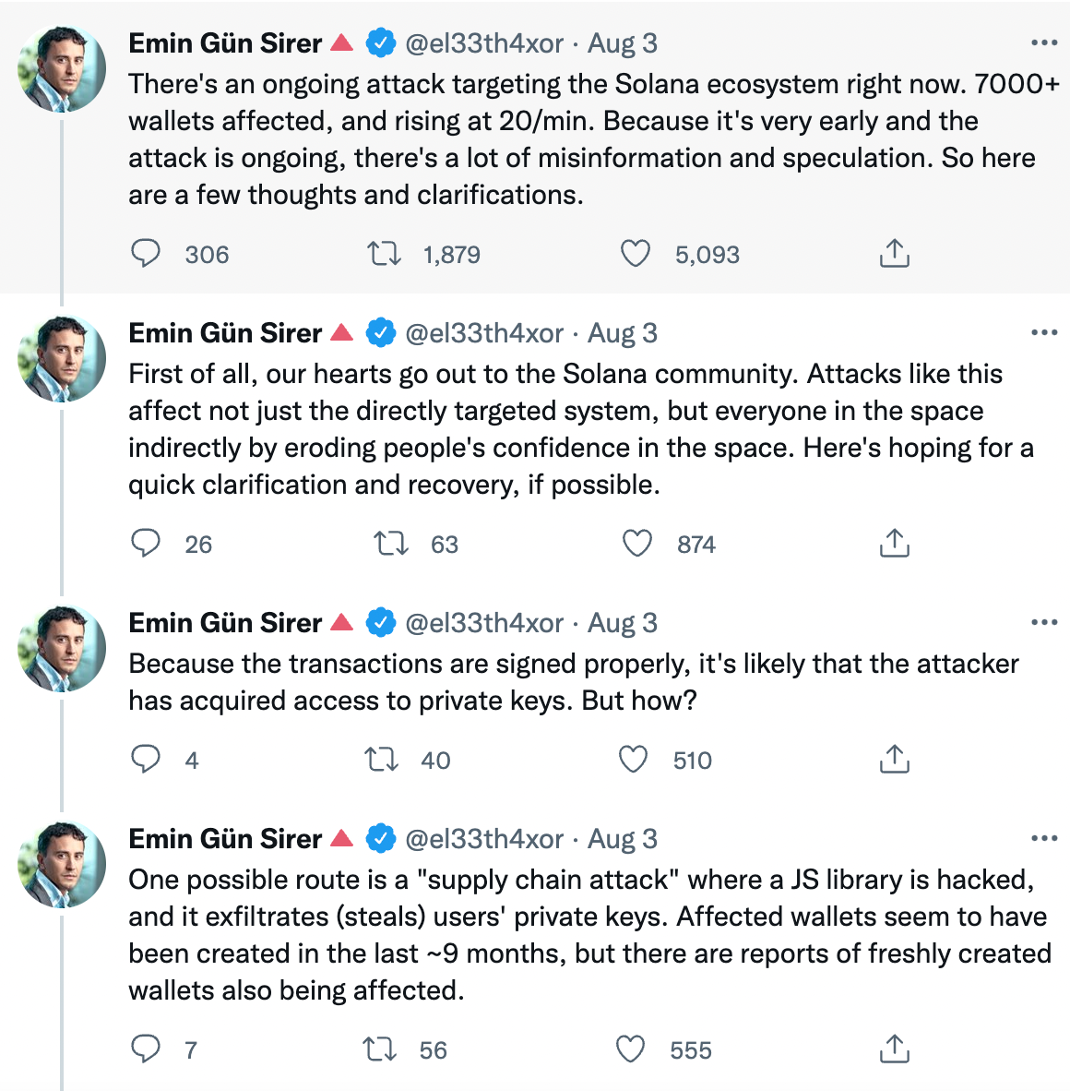
Subsequently, Avalanche founder Emin Gün Sirer tweeted that “There’s an ongoing attack targeting the Solana ecosystem right now. 7000+ wallets affected, and rising at 20/min.”
He also suggested that (according to the on-chain statistics) “because the transactions are signed properly, it’s likely that the attacker has acquired access to private keys. But how?” Avalanche’s founder went on to explain that “one possible route is a ‘supply chain attack’ where a JS library is hacked, and it exfiltrates (steals) users’ private keys. Affected wallets seem to have been created in the last ~9 months, but there are reports of freshly created wallets also being affected.”
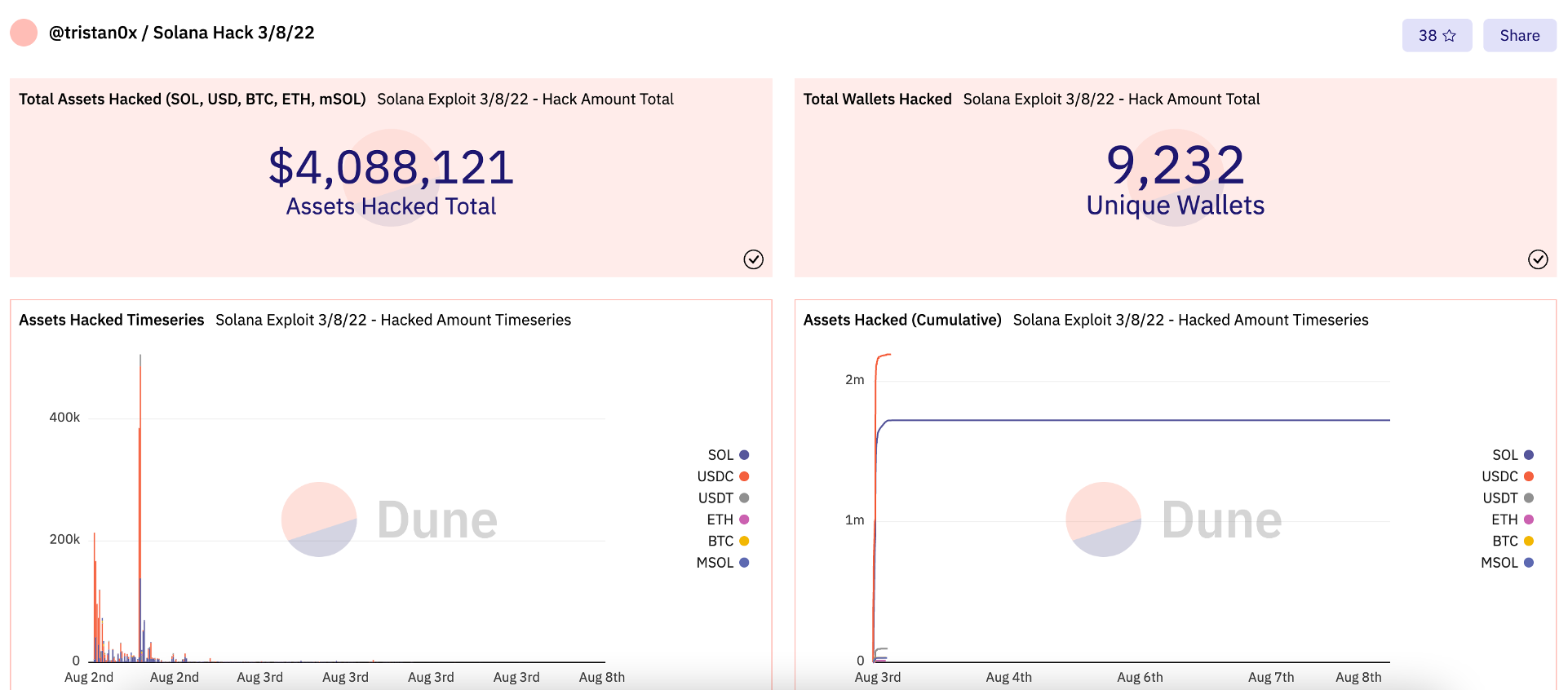
To date, over 9,200 independent wallets have been hit by the huge Solana hack, resulting in a loss of over $4.08 million, according to Dune Analytics.
Review
Hack events on such a large scale are rare even in the crypto space. In the past, most security breaches happened to exchanges, cross-chain bridges, or application protocols because they concentrate funds and hackers could exploit code loopholes to steal funds in one go. Funds stored in the wallets of regular users, on the other hand, are scattered around, and hacking wallets one by one is a complicated task. Beyond doubt, the Solana hack has attracted the attention of everyone in the crypto industry.
Right now, many security teams are looking into the hack. Anatoly Yakovenko, the cofounder of Solana Labs, tweeted that, according to the results of the latest analysis, the attack “seems like an iOS supply chain attack. Multiple plausible wallets that only received sol and had no interactions beyond receiving have been affected. As well as key that were imported into iOS, and generated externally.”
SlowMist’s security team discovered that the mnemonics of about 30% of the victims might be collected by Sentry’s services that are used by Slope Wallet and sent to its servers and that hackers could gain access to a huge number of private keys and steal users’ assets by attacking the servers. However, the team also said that it is still unclear as to how the hack happened because they did not yet know how the 60% of the stolen users who used Phantom Wallet became victims.
How do we guard against similar security risks?
As many security teams suspect, the security breach happened because private keys, upstream of the supply chain, were compromised. For crypto users, wallet security is a major concern, and you can protect your wallets in the following ways:
1、Try to use decentralized wallets as much as possible. Centralized wallets upload your private key to the server, which poses great security risks, and you might lose your assets once the database is attacked.
2、Take good care of the private key and mnemonics, and refrain from mentioning such sensitive information on the Internet or uploading them to any platform.
3、Be sure to stop the loss as soon as possible in the event of a wallet hack. Upon noticing that your assets are being drained by hackers, please transfer the remaining assets securely as soon as possible. For instance, you could outrun the hackers by accelerating your transactions. Or you could also freeze the assets on the chain (some cryptos and apps allow users to freeze their assets). If you notice that your assets have been transferred to a CEX, you can also contact the exchange to mitigate the risk.
Today, crypto assets have become a major part of many portfolios, and the significance of asset security cannot be overemphasized. While using cryptos, we should take extra caution to avoid falling victim to a security breach.








